Version (relevant - OpenSearch/Dashboard/Server OS/Browser):
OpenSearch 1.3.6 docker image
Describe the issue:
deploy a statefulset with docker image v1.3.6 in k8s. Set the environment variable: bootstrap.memory_lock=true, and after the container started, it failed to lock the memory, and output these information:
2023-02-07 21:03:17 [2023-02-07T13:03:17,021][WARN ][o.o.b.JNANatives ] [1161fe6d39a9] Unable to lock JVM Memory: error=12, reason=Cannot allocate memory
2023-02-07 21:03:12 WARNING: A terminally deprecated method in java.lang.System has been called
2023-02-07 21:03:12 WARNING: System::setSecurityManager has been called by org.opensearch.bootstrap.OpenSearch (file:/usr/share/opensearch/lib/opensearch-2.5.0.jar)
2023-02-07 21:03:12 WARNING: Please consider reporting this to the maintainers of org.opensearch.bootstrap.OpenSearch
2023-02-07 21:03:12 WARNING: System::setSecurityManager will be removed in a future release
2023-02-07 21:03:17 [2023-02-07T13:03:17,023][WARN ][o.o.b.JNANatives ] [1161fe6d39a9] This can result in part of the JVM being swapped out.
2023-02-07 21:03:17 [2023-02-07T13:03:17,024][WARN ][o.o.b.JNANatives ] [1161fe6d39a9] Increase RLIMIT_MEMLOCK, soft limit: 65536, hard limit: 65536
2023-02-07 21:03:17 [2023-02-07T13:03:17,025][WARN ][o.o.b.JNANatives ] [1161fe6d39a9] These can be adjusted by modifying /etc/security/limits.conf, for example:
2023-02-07 21:03:17 # allow user 'opensearch' mlockall
2023-02-07 21:03:17 opensearch soft memlock unlimited
2023-02-07 21:03:17 opensearch hard memlock unlimited
2023-02-07 21:03:17 [2023-02-07T13:03:17,025][WARN ][o.o.b.JNANatives ] [1161fe6d39a9] If you are logged in interactively, you will have to re-login for the new limits to take effect.
And then i build my own image using tarball and centos7,
ARG UID=1000
ARG GID=1000
ARG OPENSEARCH_HOME=/usr/share/opensearch
RUN groupadd -g $GID opensearch \
&& adduser -u $UID -g $GID -d $OPENSEARCH_HOME opensearch \
&& echo "" >> /etc/security/limits.conf \
&& echo "root soft memlock unlimited" >> /etc/security/limits.conf \
&& echo "root hard memlock unlimited" >> /etc/security/limits.conf \
&& echo "opensearch soft memlock unlimited" >> /etc/security/limits.conf \
&& echo "opensearch hard memlock unlimited" >> /etc/security/limits.conf
COPY --chown=1000:1000 ./opensearch-1.3.6 /usr/share/opensearch
WORKDIR /usr/share/opensearch
RUN echo "export JAVA_HOME=$OPENSEARCH_HOME/jdk" >> /etc/profile.d/java_home.sh \
&& echo "export PATH=\$PATH:\$JAVA_HOME/bin" >> /etc/profile.d/java_home.sh
ENV JAVA_HOME=/usr/share/opensearch/jdk
ENV PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/usr/share/opensearch/jdk/bin:/usr/share/opensearch/bin
ENV LD_LIBRARY_PATH=:/usr/share/opensearch/plugins/opensearch-knn/lib
ENV DISABLE_INSTALL_DEMO_CONFIG=true
ARG DISABLE_SECURITY_PLUGIN=true
RUN /bin/sh -c ./opensearch-onetime-setup.sh
EXPOSE 9200/tcp 9300/tcp 9600/tcp 5601/tcp
ENTRYPOINT ["./opensearch-docker-entrypoint.sh"]
CMD ["opensearch"]
Main content in opensearch-docker-entrypoing.sh is:
if [[ "$(id -u)" == "0" ]]; then
# Start opensearch
echo "OpenSearch cannot run as root. We will start opensearch with user[id: 1000]"
su opensearch
exec chroot --userspec "1000:1000" "/" "$@" "${opensearch_opts[@]}" & OPENSEARCH_PID=$!
# Start performance analyzer agent
exec chroot --userspec "1000:1000" "/" $OPENSEARCH_HOME/bin/opensearch-performance-analyzer/performance-analyzer-agent-cli > $OPENSEARCH_HOME/logs/performance-analyzer.log 2>&1 & PA_PID=$!
else
# Start opensearch
echo "OpenSearch will run as user[id: 1000]."
"$@" "${opensearch_opts[@]}" &
OPENSEARCH_PID=$!
# Start performance analyzer agent
$OPENSEARCH_HOME/bin/opensearch-performance-analyzer/performance-analyzer-agent-cli > $OPENSEARCH_HOME/logs/performance-analyzer.log 2>&1 &
PA_PID=$!
fi
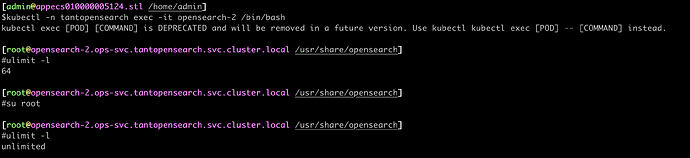
Still, it failed to lock memory even the limits.conf contains right config. Then, i logged into the container with user root, and exec the commands, the limits.conf works after i re-login user root or user opensearch.
My Question is: how to build an docker image which can lock memory in k8s statefulset?
any advice would be appreciated. thank you.