Versions (relevant - OpenSearch/Dashboard/Server OS/Browser):
2.18
Describe the issue:
A read only user is getting an error when opening dashboards about not being able to save settings. In developer console this seems to point to:
Request URL: https://host:7180/api/opensearch-dashboards/settings
Request Method: POST
Status Code: 403 Forbidden
Configuration:
{
“readall_sai”: {
“reserved”: false,
“hidden”: false,
“cluster_permissions”: [
“"
],
“index_permissions”: [
{
“index_patterns”: [
"”
],
“fls”: ,
“masked_fields”: ,
“allowed_actions”: [
“index”,
“search”,
“read”,
“indices_all”,
“indices_monitor”,
“get”,
“data_access”,
“indices:admin/mapping/put”,
“indices:admin/settings/update”
]
}
],
“tenant_permissions”: [
{
“tenant_patterns”: [
“*”
],
“allowed_actions”:
}
],
“static”: false
}
}
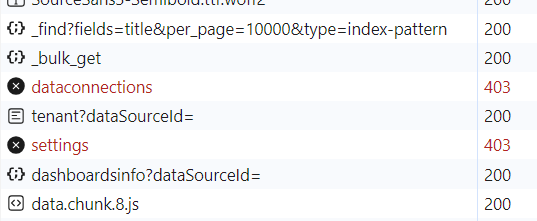
Relevant Logs or Screenshots:
What permissions need to be given? I also added this user to the opensearch_dashboards.yml readonly users settings. Perhaps it’s not needed there? Technically this setting should not then require any write access.
opensearch_security.readonly_mode.roles: [“readall_sai”,“readall”,“readall_and_monitor”,“tom_role”]