Versions (relevant - OpenSearch/Dashboard/Server OS/Browser): Opensearch 2.19.2
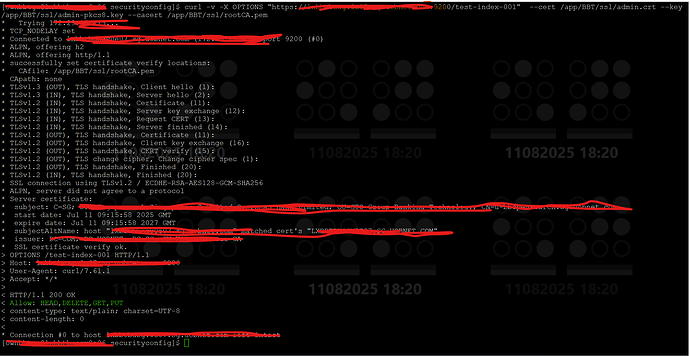
Describe the issue: We have VA Scan Vulnerability on opensearch 9200 port that states - “DELETE method found via OPTIONS banner” http-delete-method-enabled
We have to fix this VA Scan issue on 9200 and need possible steps please ? and what i have to add in opensearch.yml and this issue coming om 9200 port not apache or nginc port 443.
opensearch.yml - My Configuration;
cluster.name: opensearch-cluster
node.name: hostname
node.roles: \[master, data\]
action.auto_create_index: “.watches,.triggered_watches,.watcher-history-\*”
network.host: hostname
network.bind_host: hostname
network.publish_host: hostname
http.port: 9200
transport.port: 9300
discovery.seed_hosts:
* hostname1:9300
* hostname2:9300
* hostname3:9300
cluster.initial_cluster_manager_nodes:
* hostname1
* hostname2
* hostname3
######## Start OpenSearch Security Demo Configuration ########
plugins.security.ssl.transport.enabled: true
plugins.security.ssl.transport.pemcert_filepath: “/app/BBT/ssl//server.crt”
plugins.security.ssl.transport.pemkey_filepath: “/app/BBT/ssl/server_privatedecrypt.key”
plugins.security.ssl.transport.pemtrustedcas_filepath: “/app/BBT/ssl/rootCA.pem”
plugins.security.ssl.transport.enabled_protocols:
* TLSv1.3
* TLSv1.2
plugins.security.ssl.http.enabled_ciphers:
* “TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256”
* “TLS_ECDHE_ECDSA_WITH_CHACHA20_POLY1305_SHA256”
* “TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256”
* “TLS_ECDHE_RSA_WITH_CHACHA20_POLY1305_SHA256”
* “TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384”
* “TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384”
plugins.security.ssl.transport.enforce_hostname_verification: false
plugins.security.ssl.http.enabled: true
plugins.security.ssl.http.pemcert_filepath: “/app/BBT/ssl/server.crt”
plugins.security.ssl.http.pemkey_filepath: “/app/BBT/ssl/server_privatedecrypt.key”
plugins.security.ssl.http.pemtrustedcas_filepath: “/app/BBT/ssl/rootCA.pem”
plugins.security.ssl.http.enabled_protocols:
* TLSv1.3
* TLSv1.2
plugins.security.ssl.transport.enabled_ciphers:
* “TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256”
* “TLS_ECDHE_ECDSA_WITH_CHACHA20_POLY1305_SHA256”
* “TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256”
* “TLS_ECDHE_RSA_WITH_CHACHA20_POLY1305_SHA256”
* “TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384”
* “TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384”
plugins.security.nodes_dn:
* "CN=\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*
plugins.security.allow_unsafe_democertificates: true
plugins.security.allow_default_init_securityindex: true
plugins.security.authcz.admin_dn: \[‘CN=\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*’\]
plugins.security.audit.type: internal_opensearch
plugins.security.enable_snapshot_restore_privilege: true
plugins.security.check_snapshot_restore_write_privileges: true
plugins.security.restapi.roles_enabled: \[“all_access”\]
plugins.security.restapi.endpoints_disabled:
"*": \[“DELETE”\]
plugins.security.system_indices.enabled: true
plugins.security.system_indices.indices: \[.opensearch-security, .plugins-ml-agent, .plugins-ml-config, .plugins-ml-connector,
.plugins-ml-controller, .plugins-ml-model-group, .plugins-ml-model, .plugins-ml-task,
.plugins-ml-conversation-meta, .plugins-ml-conversation-interactions, .plugins-ml-memory-meta,
.plugins-ml-memory-message, .plugins-ml-stop-words, .opendistro-alerting-config,
.opendistro-alerting-alert*, .opendistro-anomaly-results\*, .opendistro-anomaly-detector\*,
.opendistro-anomaly-checkpoints, .opendistro-anomaly-detection-state, .opendistro-reports-*,
.opensearch-notifications-*, .opensearch-notebooks, .opensearch-observability, .ql-datasources,
.opendistro-asynchronous-search-response\*, .replication-metadata-store, .opensearch-knn-models,
.geospatial-ip2geo-data\*, .plugins-flow-framework-config, .plugins-flow-framework-templates,
.plugins-flow-framework-state\]
node.max_local_storage_nodes: 3
Configuration:
roles.yml:
\_meta:
type: “roles”
config_version: 2
readonly_role:
cluster_permissions:
- cluster:monitor/\*
index_permissions:
- index_patterns:
- ‘\*’
allowed_actions:
- read
- write
# No delete permission
roles_mapping.yml
---
# In this file users, backendroles and hosts can be mapped to Security roles.
# Permissions for OpenSearch roles are configured in roles.yml
\_meta:
type: “rolesmapping”
config_version: 2
all_access:
reserved: false
backend_roles:
* “admin”
description: “Maps admin to all_access”
readonly_role:
users:
- “readonly”
internal_users.yml
---
# This is the internal user database
# The hash value is a bcrypt hash and can be generated with plugin/tools/hash.sh
\_meta:
type: “internalusers”
config_version: 2
# Define your internal users here
## Demo users
admin:
hash: “$2y$12$eeszaFEDaVTCEPjGJT9Q3ebUX1SEg2IjB/JLgs0shGsFW6IUjSHPy”
reserved: true
backend_roles:
* “admin”
description: “Admin user”
bitbucket:
hash: “$2y$12$eeszaFEDaVTCEPjGJT9Q3ebUX1SEg2IjB/JLgs0shGsFW6IUjSHPy”
backend_roles:
* “admin”
description: “Admin user”
readonly:
hash: “$2y$12$eeszaFEDaVTCEPjGJT9Q3ebUX1SEg2IjB/JLgs0shGsFW6IUjSHPy” # hashed password
reserved: false
backend_roles: [ ]
description: “Read-only user”
Relevant Logs or Screenshots: