Versions (relevant - OpenSearch/Dashboard/Server OS/Browser): 2.19.1
Describe the issue:
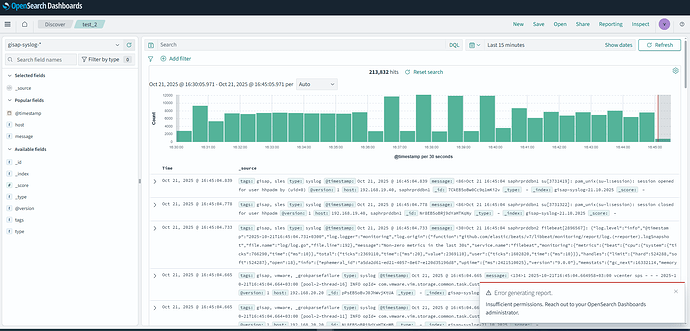
Users can successfully generate reports in OpenSearch Dashboards → Reporting, but when trying to download the generated XLSX or CSV file, the following error appears:
“Insufficient permissions. Reach out to your OpenSearch Dashboards administrator.”
What works:
-
Reports are successfully created and listed under Reporting → Reports.
-
The report status is Shared, and the file link (e.g., “XLSX”) appears as expected.
-
The problem occurs only when downloading the file.
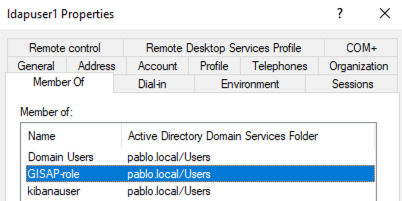
Current Role Configuration:
-
The user’s backend role is mapped to:
-
reports_full_access -
asynchronous_search_full_access -
kibana_user -
Custom role
GISAP-index
-
-
GISAP-indexincludes:-
cluster:admin/opendistro/reports/*actions -
Full index permissions for
.opendistro-reports-*,.opensearch_dashboards*,.kibana* -
Action groups:
read,write,index,manage,create_index
-
-
System indices are enabled in
opensearch.yml(plugins.security.system_indices.enabled: true).
Troubleshooting Done:
-
Verified access to
.opendistro-reports-*indices → OK -
No
security_exceptionor “no permissions for” messages in OpenSearch logs. -
Adding
kibana_all_readandkibana_all_writeto.opensearch_dashboards*did not resolve the issue. -
Reports appear under the user’s tenant; however, download still fails.
Question:
Which specific permissions (cluster or index level) are required to allow downloading report files (XLSX/CSV)?
Or is the report download action restricted to administrative users only in OpenSearch Dashboards 2.19?
Configuration:
{
"GISAP-index": {
"reserved": false,
"hidden": false,
"cluster_permissions": \[
"cluster_composite_ops_ro",
"cluster_monitor",
"cluster:admin/opendistro/reports/definition/create",
"cluster:admin/opendistro/reports/definition/update",
"cluster:admin/opendistro/reports/definition/get",
"cluster:admin/opendistro/reports/definition/list",
"cluster:admin/opendistro/reports/instance/list",
"cluster:admin/opendistro/reports/instance/get",
"cluster:admin/opendistro/reports/menu/download",
"indices:data/write/bulk\*"
\],
"index_permissions": \[
{
"index_patterns": \[
"logs-*",
"gtsr-syslog-*",
"gtsr-beats-*"
\],
"fls": \[\],
"masked_fields": \[\],
"allowed_actions": \[
"indices:data/read/search",
"indices:data/read/get",
"indices:data/read/explain",
"indices:monitor/settings/get"
\]
},
{
"index_patterns": \[
".opendistro-reports-*"
\],
"fls": [ ],
"masked_fields": [ ],
"allowed_actions": \[
"indices:data/read/search",
"indices:data/read/get",
"indices:data/write/index",
"indices:data/write/update",
"indices:data/write/delete",
"indices:admin/create",
"indices:admin/mapping/put"
\]
},
{
"index_patterns": \[
".opensearch_dashboards\*",
".kibana\*"
\],
"fls": [ ],
"masked_fields": [ ],
"allowed_actions": \[
"kibana_all_read"
\]
}
\],
"tenant_permissions": [ ],
"static": false
}
}
Relevant Logs or Screenshots: