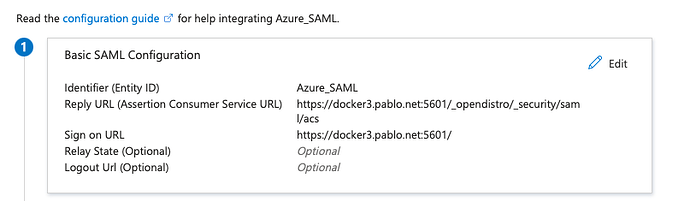
Versions (relevant - OpenSearch/Dashboard/Server OS/Browser):
Opensearch :3.0.0
Docker version 28.3.0, build 38b7060
Describe the issue:
I am trying to connect to Azure SSO for Opensearch Dashboards getting the below error
in azure login page
Sign in
Sorry, but we’re having trouble signing you in.,
AADSTS50011: The reply URL 'https://dashboard-url:5601/_opendistro/_security/saml/acs' specified in the request does not match the reply URLs configured for the application 'https://dashboard-url.net:5601'. Make sure the reply URL sent in the request matches one added to your application in the Azure portal.
Configuration:
dashboards.yml
server.name: opensearch-dashboards
server.host: "0.0.0.0"
server.port: 5601
server.ssl.enabled: true
server.ssl.certificate: /usr/share/opensearch-dashboards/config/certs/opensearch.pem
server.ssl.key: /usr/share/opensearch-dashboards/config/certs/opensearch-key.pem
server.ssl.certificateAuthorities: ["/usr/share/opensearch-dashboards/config/certs/root-ca.pem"]
opensearch.hosts: ["opensearch-url:9200"]
opensearch.ssl.verificationMode: none
opensearch.ssl.certificateAuthorities: ["/usr/share/opensearch-dashboards/config/certs/root-ca.pem"]
opensearch.username: "admin"
opensearch.password: "password"
# Request headers
#opensearch.requestHeadersWhitelist: ["authorization", "securitytenant"]
server.xsrf.allowlist: ["/_plugins/_security/saml/acs/idpinitiated", "/_opendistro/_security/saml/acs", "/_plugins/_security/saml/acs", "/_plugins/_security/saml/logout"]
opensearch_security.auth.type: "saml"
opensearch_security.auth.multiple_auth_enabled: true
# Multi-tenancy
opensearch_security.multitenancy.enabled: true
opensearch_security.multitenancy.tenants.preferred: ["Private", "Global"]
# Cookie settings
opensearch_security.cookie.secure: true
# Logging
logging.verbose: true
#logging.events: ["authentication", "security", "http", "error"]
security-config.yml
_meta:
type: "config"
config_version: 2
config:
dynamic:
http:
anonymous_auth_enabled: false
xff:
enabled: false
authc:
basic_internal_auth_domain:
description: "Internal authentication"
http_enabled: true
transport_enabled: true
order: 0
http_authenticator:
type: basic
challenge: false
authentication_backend:
type: internal
saml_auth_domain:
description: "Azure AD SAML Authentication"
http_enabled: true
transport_enabled: false
order: 1
http_authenticator:
type: saml
challenge: true
config:
idp:
pemtrustedcas_content: |-
-----BEGIN CERTIFICATE-----
XXXXXXXXXXXXXXXXXX
-----END CERTIFICATE-----
entity_id: "https://sts.windows.net/XXXXXXX/"
metadata_url: "https://login.microsoftonline.com/XXXXXXX"
sp:
entity_id: "https://dashboard-url.net:5601"
kibana_url: "https://dashboard-url.net:5601"
subject_key: "user.userprincipalname"
roles_key: "user.groups"
name_id_format: "urn:oasis:names:tc:SAML:2.0:nameid-format:persistent"
exchange_key: "8Fo_H8xxxvstUV6qahZwtzZU89XqsQYDKi4RWSrTO4o"
roles_key_is_pattern: false
verify_request_signature: false
authentication_backend:
type: noop
authz:
roles_from_myldap:
description: "Map Azure AD groups to roles"
http_enabled: true
transport_enabled: false
authorization_backend:
type: noop
do_not_fail_on_forbidden: false
multi_rolespan_enabled: true
hosts_resolver_mode: "ip-only"
I am using _pluigns instead of _opensdistro as suggested for later 2.0 versions