Just a note @Mantas; When I query in OpenSearch using admin login it works fine & gets me the data; probably admin has all_access role. But for other user from KeyCloak when they sign in; though we’ve created the mapping between OpenSearch role & Backend role/groups; but still it fails with that security exception for other users.
I can see that you are passing groups(roles_key: groups) in your Token (as per below) but I cannot see them being mapped to anything in your ../opensearch-security/roles_mapping.yml:
"groups": [
"/asia_compressor_group",
"/europe_compressor_group"
],
How are you mapping your back_end roles to OpenSearch roles?
best,
mj
Hello @Mantas,
Actually for creating the Backend role mapping between KeyCloak & OpenSearch we are using the REST API endpoints:
For creating the OS Role
_plugins/_security/api/roles/${role}
For Creating the roleMapping
_plugins/_security/api/rolesmapping/${role}
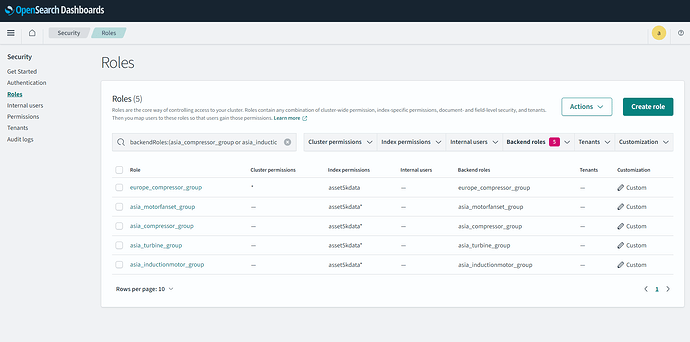
We can see all the roles in Opensearch dashboard under Security
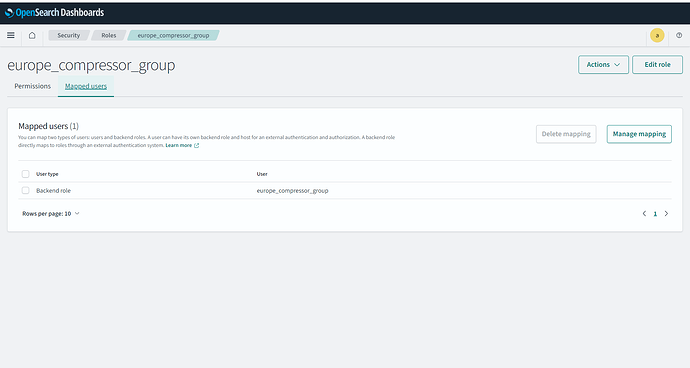
& if we go inside any of the role we can see it’s Backend role mapped to:
Can you add "/europe_compressor_group" with / to the mapping and test it again?
Hello @Mantas,
You rightly identified the issue, extra / was causing the issue that is coming from KeyCloak; we disabled the FullPath flag for the groups Client scope & we are able to fetch the records.
Thanks a ton @Mantas; really appreciated!
You are welcome, glad to help!
Hi vishal,
I am currently working on integrating keycloak with opensearch. I running opensearch from the helm charts. It would be helpful if you guide me thorugh the integration steps. I tried with some configuration it didn’t worked.
Can anyone help me on this
@Gurs Could you open a new thread and share your values.yml file and OpenSearch version?
Hi Pablo, I am not able to share the values.yaml as it huge and here in this chat going beyond the accepted limit,have shared opensearchdashboard.yml, config.yml and opensearch.yml. As an add on I am using the alice user while login the keycloak page which is having the neccesary roles assigned in role.yml and it do have the backend role mapped in role mapping.
dashboard.yml
# Copyright OpenSearch Contributors
# SPDX-License-Identifier: Apache-2.0
# Default configuration for OpenSearch Dashboards
# The URLs of the OpenSearch instances to use for all your queries
opensearch.hosts:
opensearch.username: "admin"
opensearch.password: "S6iu^sEWpsQjDCtn"
# OpenSearch Dashboards authentication using OpenID Connect
opensearch_security.auth.type: "openid"
opensearch_security.openid.client_id: "opensearchdashboard"
opensearch_security.openid.client_secret: "QvVZCaNzxhGdlxTZD5SHbtieNUjVaX7m"
opensearch_security.openid.connect_url: "https://keycloak.prod.npas-nam3.ch-dc-os-dhn-025.k8s.dyn.net/realms/master/.well-known/openid-configuration"
opensearch_security.openid.base_redirect_url: "https://opensearch-dashboards.cluster.prod.npas-nam3.ch-dc-os-dhn-025.k8s.dyn.net"
# Optional: Enable multitenancy
# opensearch_security.multitenancy.enabled: true
# opensearch_security.multitenancy.tenants.preferred:
# - Private
# - Global
# Optional: Set roles for OpenSearch Dashboards if needed
# opensearch_security.readonly_mode.roles:
# - kibana_read_only
# Server Settings
server:
host: "0.0.0.0"
port: 5601
ssl:
enabled: true
certificate: "/opt/bitnami/opensearch-dashboards/config/certs/server/tls.crt"
key: "/opt/bitnami/opensearch-dashboards/config/certs/server/tls.key"
# OpenSearch SSL settings
opensearch.ssl.verificationMode: none
opensearch.ssl.certificateAuthorities:
- "/opt/bitnami/opensearch-dashboards/config/certs/opensearch/ca.crt"
# Set the headers to be sent to OpenSearch
opensearch.requestHeadersWhitelist:
- authorization
- securitytenant
# Enable cookie security (set to false for HTTP, true for HTTPS)
opensearch_security.cookie.secure: false
# Specify the path to store the OpenSearch Dashboards data
path:
data: "/bitnami/opensearch-dashboards/data"
# Specify the PID file location
pid:
file: "/opt/bitnami/opensearch-dashboards/tmp/opensearch-dashboards.pid"
# Set logging configuration
logging:
dest: stdout
verbose: true
# Specify locale
i18n.locale: "en"
opensearch.yml
http:
port: "9200"
path:
data: /bitnami/opensearch/data
transport:
port: "9300"
network:
host: opensearch-coordinating-0.opensearch-coordinating-hl.sparknet-applications.svc.cluster.local
publish_host: opensearch-coordinating-0.opensearch-coordinating-hl.sparknet-applications.svc.cluster.local
bind_host: 0.0.0.0
cluster:
name: open
node:
name: opensearch-coordinating-0
roles: []
discovery:
seed_hosts:
- opensearch-master-hl.sparknet-applications.svc.cluster.local
- opensearch-coordinating-hl.sparknet-applications.svc.cluster.local
- opensearch-data-hl.sparknet-applications.svc.cluster.local
- opensearch-ingest-hl.sparknet-applications.svc.cluster.local
initial_state_timeout: 10m
plugins:
security:
nodes_dn:
- CN=opensearch-master
- CN=opensearch-data
- CN=opensearch-coordinating
- CN=opensearch-ingest
authcz:
admin_dn:
- CN=admin
- CN=admin
ssl:
http:
enabled: "true"
pemkey_filepath: /opt/bitnami/opensearch/config/certs/tls.key
pemcert_filepath: /opt/bitnami/opensearch/config/certs/tls.crt
pemtrustedcas_filepath: /opt/bitnami/opensearch/config/certs/ca.crt
transport:
enabled: "true"
enforce_hostname_verification: false
pemkey_filepath: /opt/bitnami/opensearch/config/certs/tls.key
pemcert_filepath: /opt/bitnami/opensearch/config/certs/tls.crt
pemtrustedcas_filepath: /opt/bitnami/opensearch/config/certs/ca.crt
redirecting to the keycloak login page after providing the credentials getting below error
“statusCode”:401,“error”:“Unauthorized”,“message”:“Unauthorized”}