@wh1test When you open a browser, do you use http://172.16.1.7:5601 as starting point or FQDN?
@wh1test This is my working example
User has only realm roles assigned. No groups.
config.yml
---
_meta:
type: "config"
config_version: 2
config:
dynamic:
http:
anonymous_auth_enabled: false
xff:
enabled: false
internalProxies: "192\\.168\\.0\\.10|192\\.168\\.0\\.11"
authc:
basic_internal_auth_domain:
description: "Authenticate via HTTP Basic against internal users database"
http_enabled: true
transport_enabled: true
order: 0
http_authenticator:
type: "basic"
challenge: false
authentication_backend:
type: "intern"
openid_auth_domain:
http_enabled: true
transport_enabled: true
order: 1
http_authenticator:
type: "openid"
challenge: false
config:
subject_key: "preferred_username"
roles_key: "roles"
openid_connect_url: "https://dockerhub.pablo.local:8443/realms/opensearch/.well-known/openid-configuration"
openid_connect_idp.pemtrustedcas_filepath: "/usr/share/opensearch/config/keycloak.crt"
openid_connect_idp.enable_ssl: true
skip_users:
- "kibanaro"
- "kibanaserver"
- "logstash"
- "adminp"
- "fliebeat_internal"
- "kibanauser"
authentication_backend:
type: "noop"
opensearch_dashboards.yml
server.name: kibana
server.host: "0.0.0.0"
server.customResponseHeaders : { "Access-Control-Allow-Credentials" : "true" }
server.ssl.enabled: true
server.ssl.certificate: /usr/share/opensearch-dashboards/config/opensearch_dashboards.crt
server.ssl.key: /usr/share/opensearch-dashboards/config/opensearch_dashboards.key
opensearch.ssl.verificationMode: none
opensearch.username: kibanaserver
opensearch.password: kibanaserver
opensearch.requestHeadersWhitelist: ["securitytenant","Authorization"]
opensearch_security.multitenancy.enabled: true
opensearch_security.multitenancy.tenants.preferred: ["Global","Private"]
opensearch_security.multitenancy.tenants.enable_private: false
opensearch_security.readonly_mode.roles: ["kibana_read_only"]
#OpenID authentication - keycloak
opensearch_security.auth.type: ["basicauth","openid"]
opensearch_security.auth.multiple_auth_enabled: true
opensearch_security.openid.connect_url: "https://dockerhub.pablo.local:8443/realms/opensearch/.well-known/openid-configuration"
opensearch_security.openid.client_id: "docker2-openid"
opensearch_security.openid.root_ca: "/usr/share/opensearch-dashboards/config/keycloak.crt"
opensearch_security.openid.base_redirect_url: "https://docker2.pablo.local:5601"
opensearch_security.openid.scope: openid profile email
opensearch_security.cookie.secure: false
I’m very appreciated you, Pablo. I followed your screenshots step by step, but in this way I’m not able to assign a role to a user.
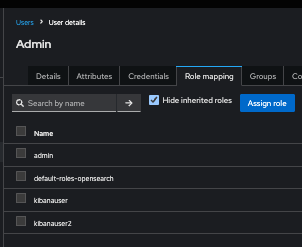
My Realm Roles:
My user (tried multiple users with and without group memberships). There are no os_kibanauser or os_admin role in the list =|
Upgraded my opensearch and dashboards to 2.19.3 + configured some SSL settings during fixing of post-upgrade issues appeared in logs. And finally I managed to login via keycloak!
@pablo thank you very much for your assistance! God blesses you)
But some issues still persist in logs after login completed:
Aug 25 00:05:54 opensearch opensearch-dashboards[877]: Issue in fetching data sources: StatusCodeError: Authorization Exception
Aug 25 00:05:54 opensearch opensearch-dashboards[877]: at respond (/opt/opensearch-dashboards/node_modules/elasticsearch/src/lib/transport.js:349:15)
Aug 25 00:05:54 opensearch opensearch-dashboards[877]: at checkRespForFailure (/opt/opensearch-dashboards/node_modules/elasticsearch/src/lib/transport.js:306:7)
Aug 25 00:05:54 opensearch opensearch-dashboards[877]: at HttpConnector. (/opt/opensearch-dashboards/node_modules/elasticsearch/src/lib/connectors/http.js:173:7)
Aug 25 00:05:54 opensearch opensearch-dashboards[877]: at IncomingMessage.wrapper (/opt/opensearch-dashboards/node_modules/lodash/lodash.js:4991:19)
Aug 25 00:05:54 opensearch opensearch-dashboards[877]: at IncomingMessage.emit (node:events:529:35)
Aug 25 00:05:54 opensearch opensearch-dashboards[877]: at IncomingMessage.emit (node:domain:489:12)
Aug 25 00:05:54 opensearch opensearch-dashboards[877]: at endReadableNT (node:internal/streams/readable:1400:12)
Aug 25 00:05:54 opensearch opensearch-dashboards[877]: at processTicksAndRejections (node:internal/process/task_queues:82:21) {
Aug 25 00:05:54 opensearch opensearch-dashboards[877]: status: 403,
Aug 25 00:05:54 opensearch opensearch-dashboards[877]: displayName: ‘AuthorizationException’,
Aug 25 00:05:54 opensearch opensearch-dashboards[877]: path: ‘/_plugins/_query/_datasources’,
Aug 25 00:05:54 opensearch opensearch-dashboards[877]: query: {},
Aug 25 00:05:54 opensearch opensearch-dashboards[877]: body: ‘{\n’ +
Aug 25 00:05:54 opensearch opensearch-dashboards[877]: ’ “status”: 403,\n’ +
Aug 25 00:05:54 opensearch opensearch-dashboards[877]: ’ “error”: {\n’ +
Aug 25 00:05:54 opensearch opensearch-dashboards[877]: ’ “type”: “OpenSearchSecurityException”,\n’ +
Aug 25 00:05:54 opensearch opensearch-dashboards[877]: ’ “reason”: “There was internal problem at backend”,\n’ +
Aug 25 00:05:54 opensearch opensearch-dashboards[877]: ’ “details”: “no permissions for [cluster:admin/opensearch/ql/datasources/read] and User [name\u003dyura, backend_roles\u003d, requestedTenant\u003d]”\n’ +
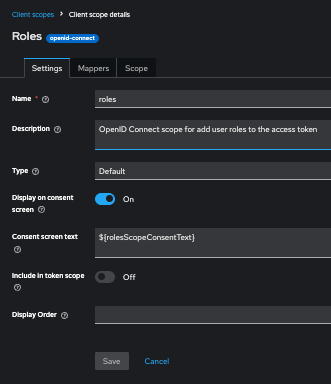
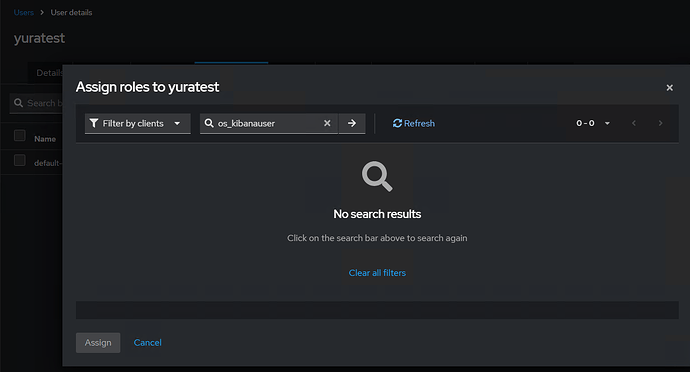
Is it possible to make opensearch read roles_key from not from “roles” tree, where a lot of useless for opensearch roles from keycloak exist, but from os_roles or from resource_acccess.opensearch.roles path?
Now I’m getting the following roles after login:
And those logs in opensearch.log:
[INFO ][o.o.s.p.PrivilegesEvaluatorImpl] [opensearch-node1] No cluster-level perm match for User [name=yuratest, backend_roles=[manage-account, default-roles-master, offline_access, os_kibanauser, manage-account-links, uma_authorization, view-profile], requestedTenant=] Resolved [aliases=[], allIndices=[], types=[], originalRequested=[], remoteIndices=] [Action [cluster:admin/opensearch/ql/datasources/read]] [RolesChecked [own_index, kibana_user]]. No permissions for [cluster:admin/opensearch/ql/datasources/read]
And opensearch-dashboards.log:
Aug 25 11:33:30 opensearch opensearch-dashboards[88726]: statusCode: 403,
Aug 25 11:33:30 opensearch opensearch-dashboards[88726]: response: ‘{\n’ +
Aug 25 11:33:30 opensearch opensearch-dashboards[88726]: ’ “status”: 403,\n’ +
Aug 25 11:33:30 opensearch opensearch-dashboards[88726]: ’ “error”: {\n’ +
Aug 25 11:33:30 opensearch opensearch-dashboards[88726]: ’ “type”: “OpenSearchSecurityException”,\n’ +
Aug 25 11:33:30 opensearch opensearch-dashboards[88726]: ’ “reason”: “There was internal problem at backend”,\n’ +
Aug 25 11:33:30 opensearch opensearch-dashboards[88726]: ’ “details”: “no permissions for [cluster:admin/opensearch/ql/datasources/read] and User [name\u003dyuratest, backend_roles\u003d[manage-account, default-roles-master, offline_access, os_kibanauser, manage-account-links, uma_authorization, view-profile], requestedTenant\u003d]”\n’ +
Aug 25 11:33:30 opensearch opensearch-dashboards[88726]: ’ }\n’ +
Aug 25 11:33:30 opensearch opensearch-dashboards[88726]: ‘}’,
Aug 25 11:33:30 opensearch opensearch-dashboards[88726]: toString: [Function (anonymous)],
Aug 25 11:33:30 opensearch opensearch-dashboards[88726]: toJSON: [Function (anonymous)]
Aug 25 11:33:30 opensearch opensearch-dashboards[88726]: }
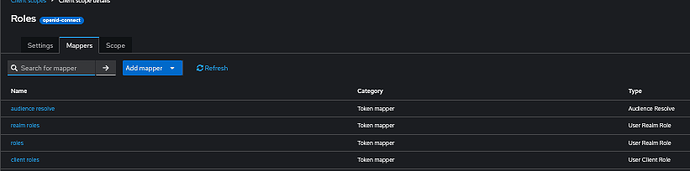
My Roles at Client level:
My Client scopes:
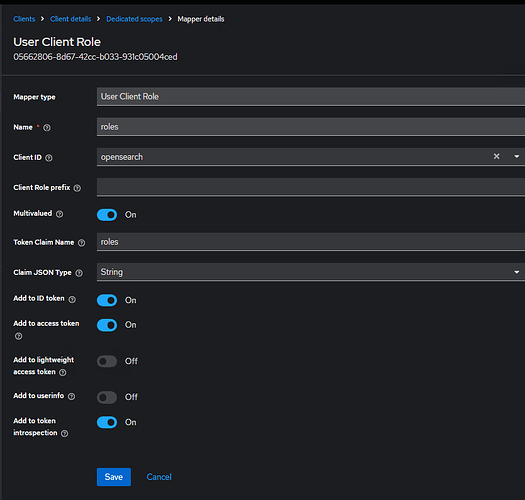
My mapper (current config, but I tried define Token Claim Name as “os_roles“ without luck):
Evaluate test result:
Evaluate test result
{
“exp”: 1756113026,
“iat”: 1756112966,
“jti”: “40a79d43-9a9a-402f-852c-0299594d9991”,
“iss”: “https://keycloak.mycorp.com/auth/realms/master”,
“aud”: “opensearch”,
“sub”: “f82fbf87-80d9-4129-bc35-372ac3365aac”,
“typ”: “ID”,
“azp”: “opensearch”,
“sid”: “fc396715-3da2-40b2-8c14-8660ddf57f00”,
“acr”: “1”,
“resource_access”: {
“opensearch”: {
“roles”: “os_kibanauser”
},
“account”: {
“roles”: “manage-account”
}
},
“email_verified”: false,
“realm_access”: {
“roles”: [
“default-roles-master”,
“offline_access”,
“uma_authorization”
]
},
“roles”: [
“default-roles-master”,
“offline_access”,
“uma_authorization”,
“os_kibanauser”
],
“name”: “Yura Test”,
“preferred_username”: “yuratest”,
“given_name”: “Yura”,
“family_name”: “Test”,
“email”: “testt@mycorp.com”
}
And my config.yml (I tried set roles_key to “os_roles: without luck - no os_ roles defined in Client fetched):
config.yml
openid_auth_domain:
http_enabled: true
transport_enabled: true
order: 1
http_authenticator:
type: openid
challenge: false
config:
subject_key: “preferred_username”
roles_key: “roles”
openid_connect_url: “https://keycloak.mycorp.com/auth/realms/master/.well-known/openid-configuration”
scope: “openid email profile”
openid_connect_idp:
enable_ssl: true
verify_hostnames: false
jwt_clock_skew_tolerance_seconds: 60
authentication_backend:
type: noop
@wh1test I’ve cleared my extra roles. Some of them are in the realm settings and are attached to any authenticated user.
I couldn’t find the way to delete or hide default-roles- realm role.
This is what I have after the cleanup
Regarding the OpenSearch Dashboards error, kibana_user role is a basic role that allows accessing the OpenSearch Dashboards UI. You must provide more permissions for a wider access.
The missing permission cluster:admin/opensearch/ql/datasources/read is not a part of the kibana_user role.
Create a new role with missing permissions and assign it to a user through backend role mapping.
Yeap! Made it already. Created role kibana_user_power (added cluster:admin/opensearch/ql/datasources/read and read * indeces). Then mapped backend_roles os_kibanauser and kibanauser there.